In today’s digital age, cybersecurity threats are evolving at an alarming pace, posing significant risks to businesses and individuals alike. Data breaches, ransomware attacks, and phishing schemes are just a few examples of the challenges organizations face. While preventive measures like firewalls and encryption are essential, they are not foolproof. When a cybersecurity incident occurs, understanding its root cause becomes critical to preventing recurrence. This is where Root Cause Analysis (RCA) comes into play.

The Role of Root Cause Analysis in Cybersecurity
RCA is a systematic approach to identifying the underlying causes of a problem. In the context of cybersecurity, RCA helps organizations move beyond surface-level fixes, such as patching vulnerabilities or resetting passwords. Instead, it digs deeper to understand why the incident happened in the first place and how to address the systemic issues that allowed it to occur.
Key Steps in Applying RCA to Cybersecurity Incidents
- Define the Problem: Document the nature of the cybersecurity incident. For example, was it unauthorized access, data leakage, or a malware infection?
- Collect Data: Gather evidence from system logs, user activity, and network monitoring tools to understand the timeline and scope of the breach.
- Identify Potential Causes: Use RCA tools like the Fishbone Diagram or the 5 Whys to analyze contributing factors such as human error, software vulnerabilities, or configuration issues.
- Determine the Root Cause: Pinpoint the primary cause of the incident, whether it’s outdated software, lack of employee training, or insufficient security protocols.
- Implement Corrective Actions: Develop and execute a plan to eliminate the root cause, such as updating systems, conducting security awareness training, or revising access control policies.
- Verify Effectiveness: Continuously monitor the implemented changes to ensure they effectively address the identified vulnerabilities.
Real-World Example: Phishing Attack
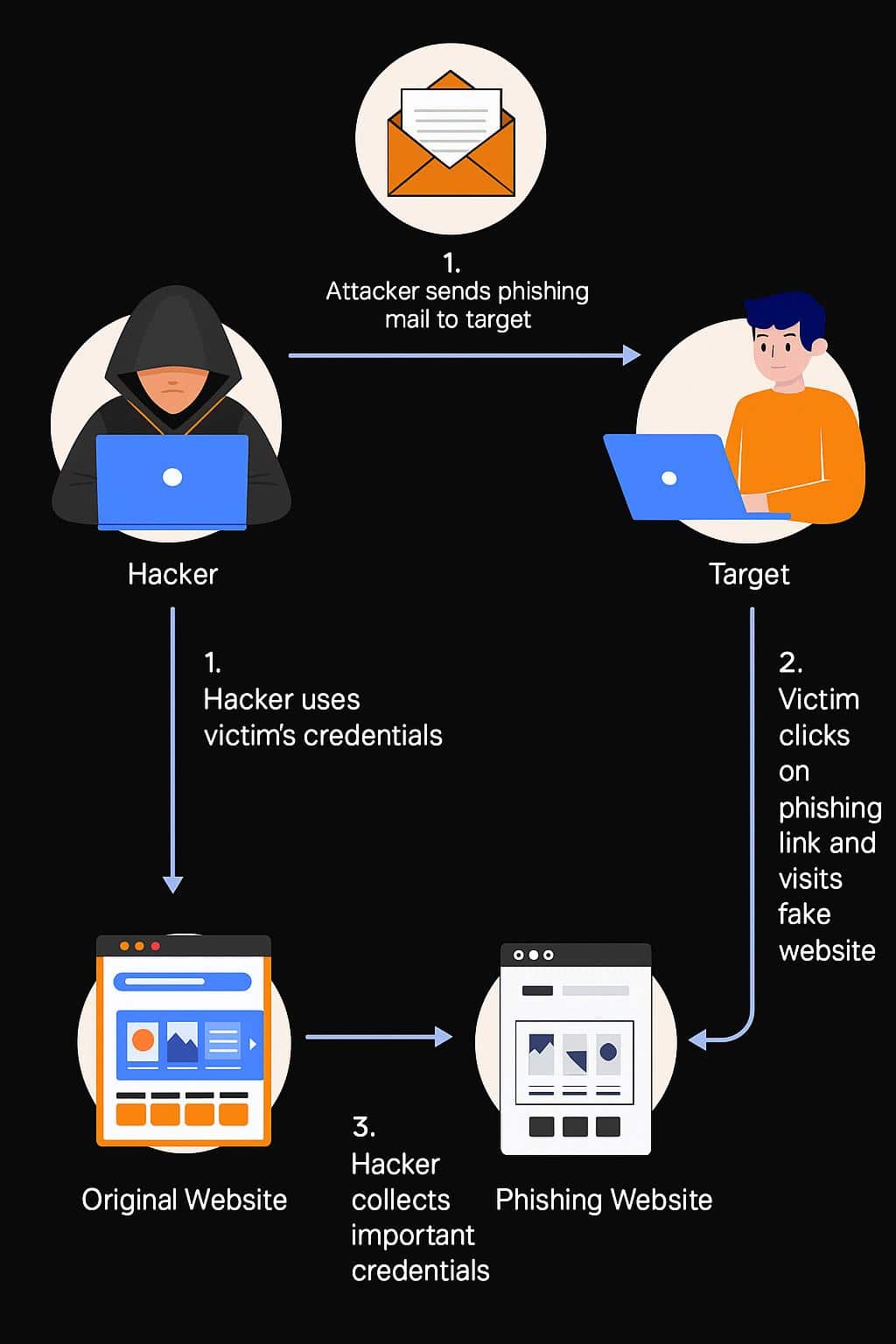
Consider a company that fell victim to a phishing attack, leading to compromised employee credentials. An RCA process might reveal that the root cause was insufficient employee training on recognizing phishing emails. The corrective action would involve implementing regular cybersecurity training and deploying advanced email filtering solutions to reduce the risk of similar incidents.
Benefits of Using RCA in Cybersecurity
- Proactive Prevention: By addressing root causes, organizations can reduce the likelihood of recurring incidents.
- Resource Optimization: RCA helps prioritize actions that provide the most significant impact on security.
- Regulatory Compliance: Thorough incident investigations demonstrate due diligence in meeting cybersecurity regulations and standards.
Conclusion
Cybersecurity incidents are inevitable, but how organizations respond can make all the difference. By incorporating Root Cause Analysis into your incident response strategy, you can uncover vulnerabilities, strengthen defenses, and build resilience against future attacks. In the battle against cyber threats, RCA is not just a problem-solving tool—it’s a vital component of a robust cybersecurity program.
Ignite your curiosity, subscribe now!
Stay informed and connected with the latest updates by subscribing today!

Recent Comments